Bitlocker is one of the most essential security features to deploy to your windows devices.
BitLocker Drive Encryption is a security feature that protects against data theft or exposure on lost, stolen, or improperly decommissioned computers. It integrates with the operating system to provide enhanced protection for files and systems, making it difficult for unauthorized users to access data on a lost or stolen computer. Additionally, BitLocker can help make data inaccessible when computers with BitLocker protection are retired or recycled. Overall, BitLocker helps to reduce the risks associated with data loss or theft.
Here is how you can silently enforce the use of bitlocker on all your windows devices. While still having full control over the decryption key, safely stored in your Microsoft tenant.
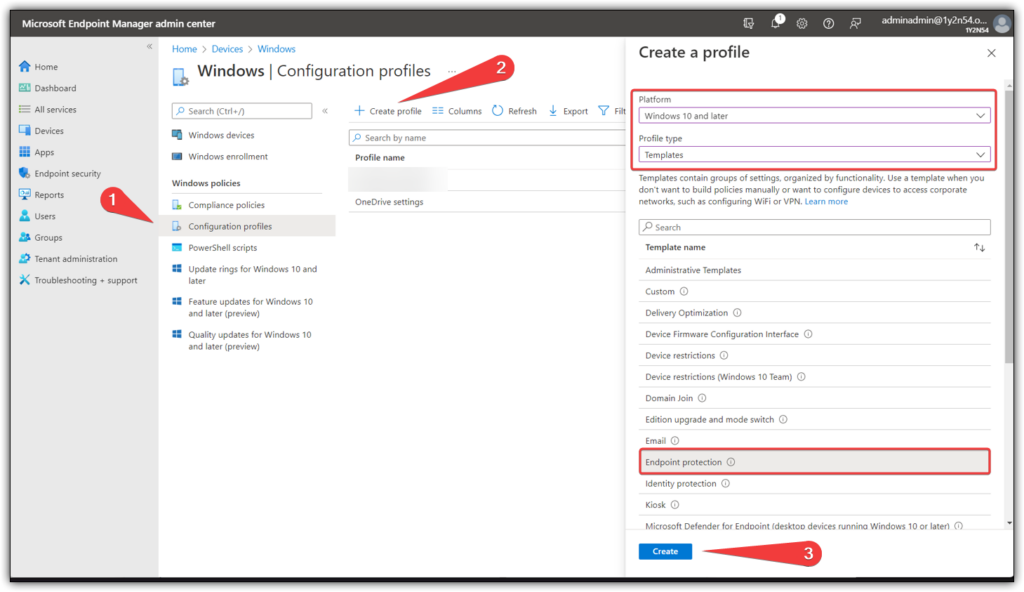
Step 1: Create Device Configuration Policy.
Start by visiting the Endpoint Manager portal, open up “Windows” under “Devices” and create a new configuration policy.
Platform: Windows 10 and later
Profile type: Templates
Template name: Endpoint Protection
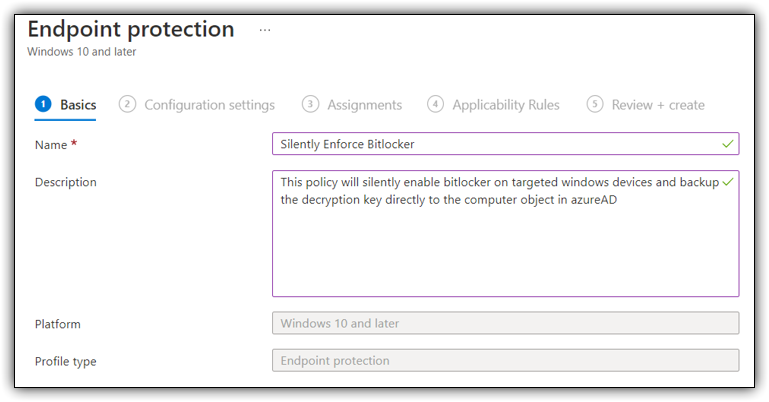
Provide a name for your policy and a brief description for your new configuration policy. Keep in mind its a great idea to be very specific so future admins know exactly what the policy does.
Name: Silently Enforce Bitlocker
Description: This Policy will silently enable bitlocker on all targeted “Windows 10 and later” devices and backup the decryption key directly to the computer object in AzureAD.
Step 2: Configure Bitlocker Settings
In the configuration settings unfold the option “Windows Encryption“
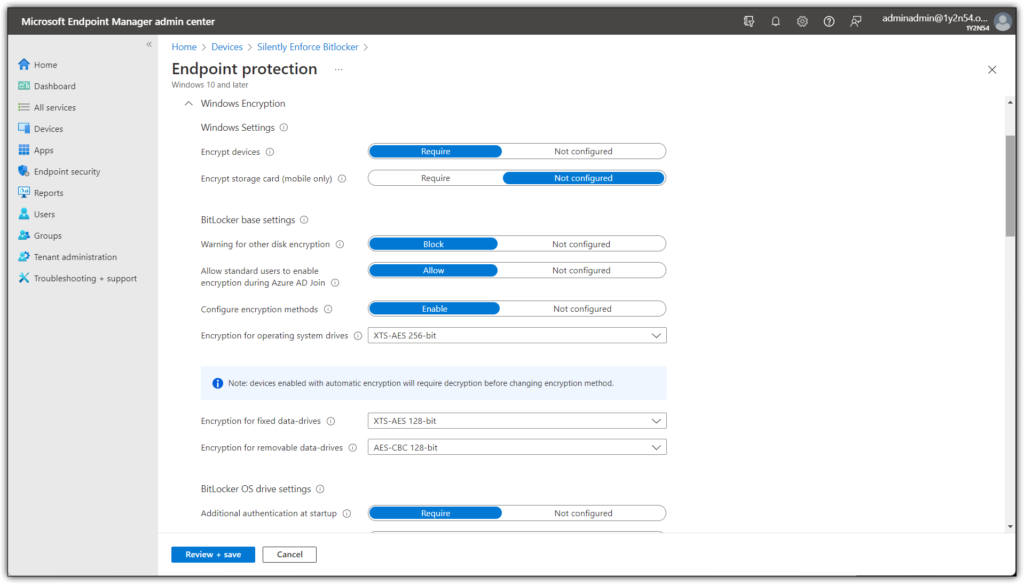
This is a rather long list of settings, below i will be providing screenshots of all the necessary settings.
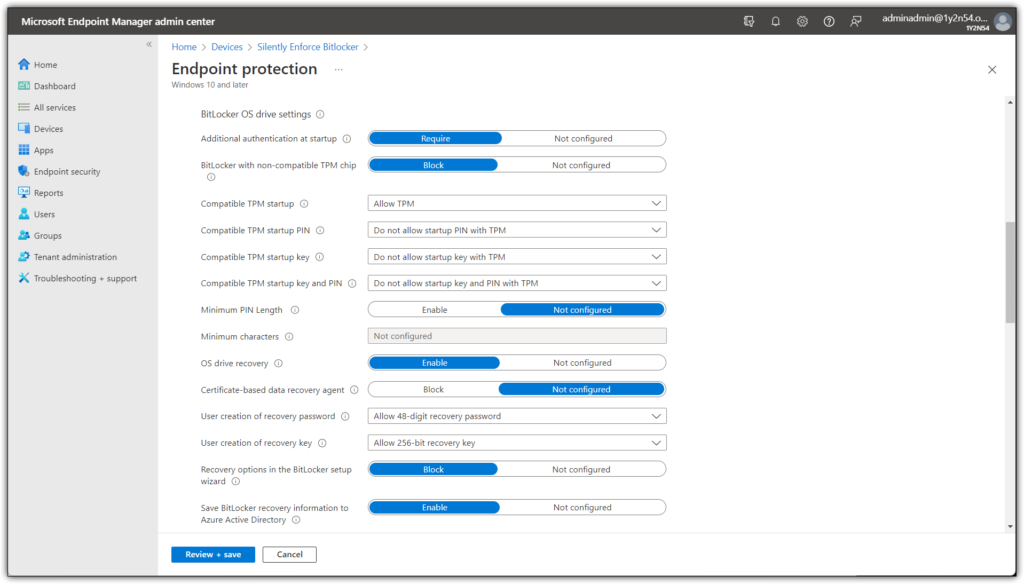
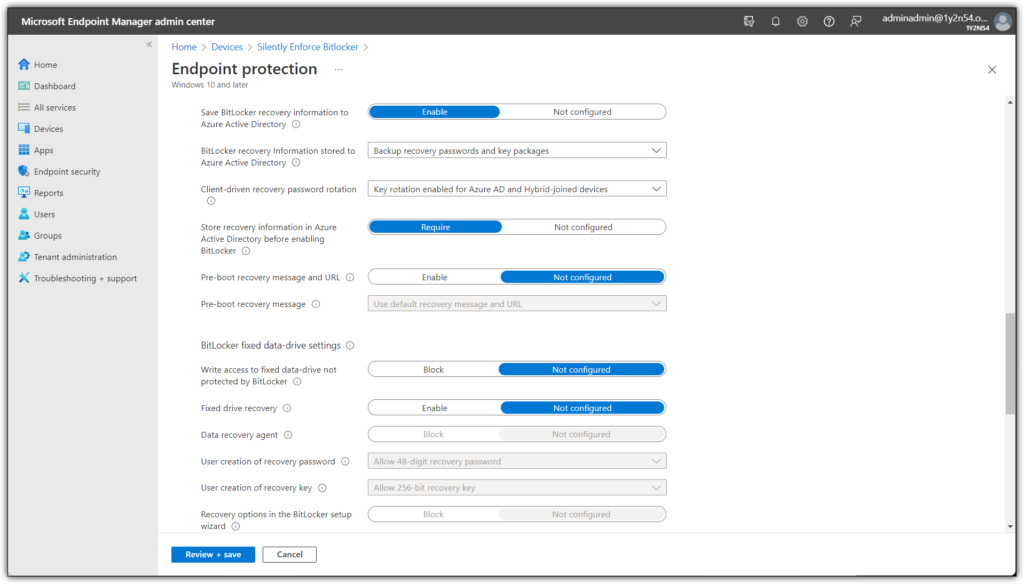
Once you have configured the settings above you need to specify which devices will be targeted by our new Bitlocker policy. As always i recommend creating “filters” whenever possible.
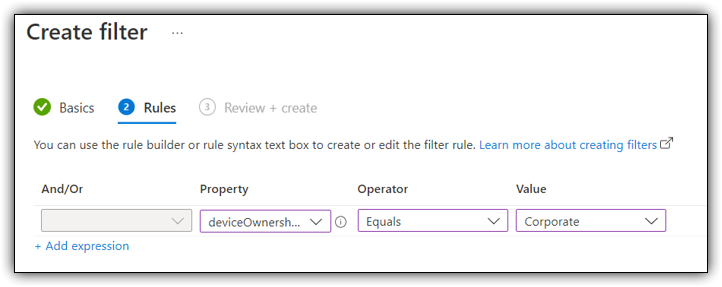
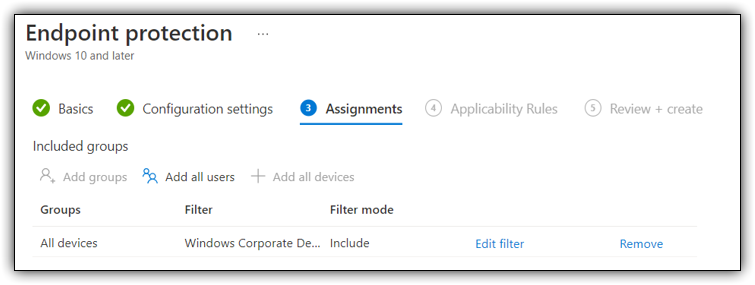
Once you have targeted the devices you want to enforce bitlocker for you can save and create the policy.
The policy will automatically start applying with no user impact. Please allow up to 30 minutes before checking the bitlocker settings on the device.
Step 3: Confirm Bitlocker Has Been Enabled
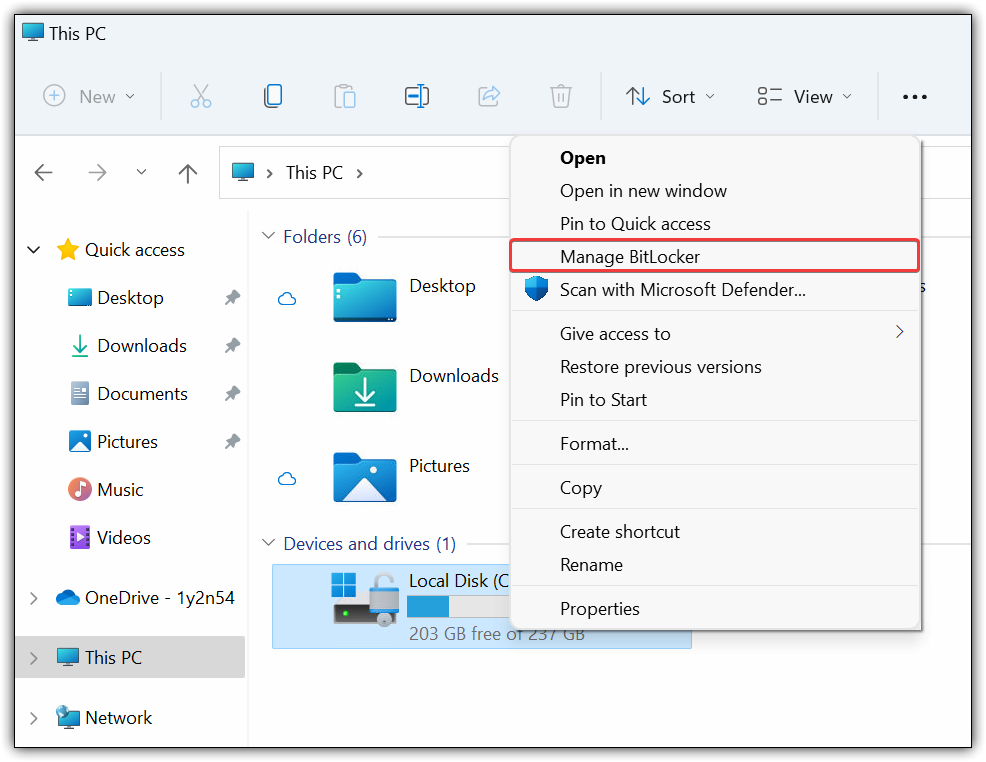
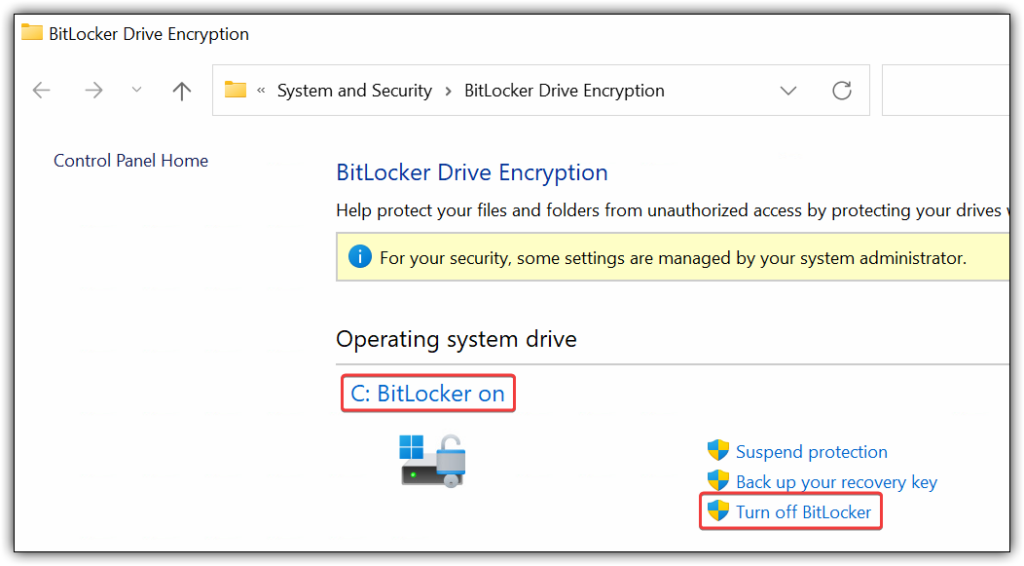
One way of confirming that your policy works is by going on one of the targeted devices and confirm bitlocker has been enabled.
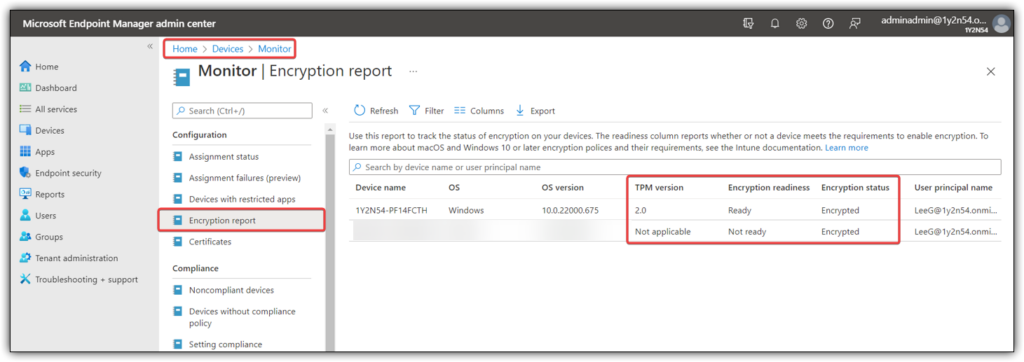
Another way is to go to the “Monitor” section of endpoint manager and choosing the “Encryption Report“. Here you can retrieve a full report of the encrypting status of all your devices, including mac devices.
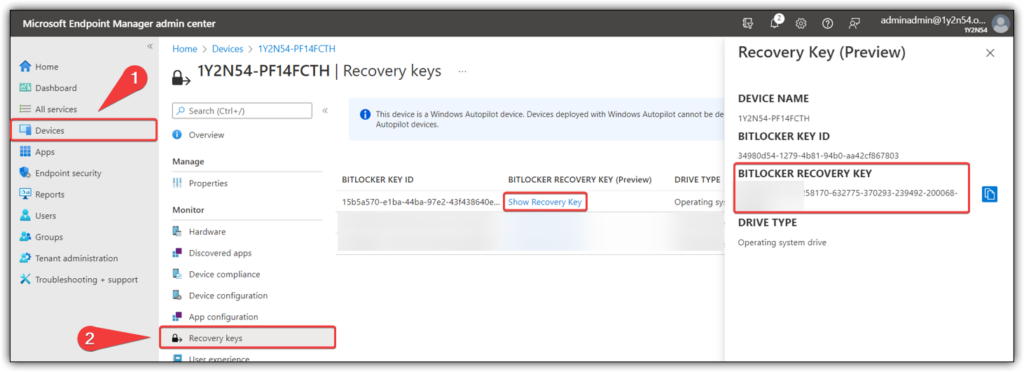
Step 4: Retrieve Bitlocker Key From AzureAD.
The most important part of configuring silent bitlocker is to be able to retrieve the decryption key from a central location.
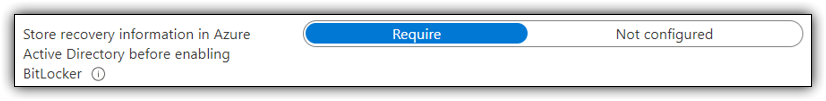
Go to the “Endpoint Manger” portal and choose devices in the left pane. Search for your device and open settings for that devices. Here you will be able to retrieve bitlocker recovery key for the device.
If you have any questions / feedback or would like to correct me on any of the stuff above, please use the comment section or contact me directly using the blue button in the bottom right corner.
